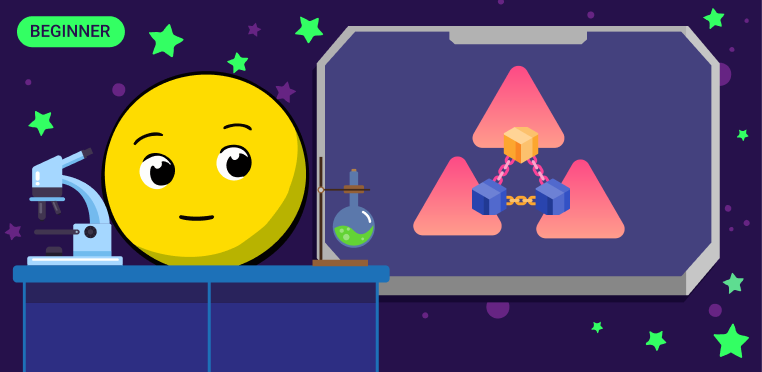
The blockchain trilemma, also known as the scalability trilemma, formulates the primary challenge of scaling distributed systems. The issue lies in the fact that the three key properties of blockchain (decentralization, security, and productivity) cannot be guaranteed to work simultaneously. A decentralized network can only have a high level of two of the three characteristics. That is, when one aspect is strengthened, the other inevitably suffers.
Before delving into the nuances of crypto trilemma, let's define scalability, security, and decentralization in general terms.
- Blockchain scalability refers to its ability to handle more transactions.
- Security refers to the ability to protect blockchain data from various attacks and prevent double-spending.
- Decentralization is a form of network redundancy that ensures the network is not controlled by a limited number of entities.
Bitcoin illustrates this. In this blockchain, the number of transactions per second is quite small, approximately seven, and blocks are mined every ten minutes. When the network is congested, transactions with low commissions can take a long time to process. The result is high levels of security and decentralization, but low productivity (aka scalability).
To enhance performance, you can increase the block size. But then the complexity will skyrocket, and in the end, only large mining pools will be able to remain on the network. As a result, the system will become more centralized. And if you reduce production time, security will be compromised. Nodes may not have sufficient time to reach a consensus before the next block is mined.
Scalability
The network involves many computers that theoretically have unlimited computing power necessary to solve various problems. Network throughput is a fundamentally significant parameter as it measures the number of transactions processed per unit of time.
Safety
Security from external exposure comes from being encrypted. Blockchain algorithms utilize modern cryptography. All transactions (entries in the blockchain) are verified through the mining procedure, which utilizes the Proof-of-Work consensus algorithm. This means that each transaction is encrypted before being added to the blockchain. Today, there is no known method to crack closed cryptographic keys. This is because the attacker needs to accomplish this within a limited time frame.
Decentralization
This feature ensures safety from internal exposure. The database (blockchain) is stored simultaneously on all participants' computers. This is one of the main properties of blockchain. It refers to the absence of any centralized body, person, or service that makes decisions on the network. Work on the network is distributed among nodes and is completely decentralized. The network algorithm provides a procedure for achieving consensus among individual nodes regarding the current state of data in the network. This mechanism is known as a consensus mechanism. To retroactively change information, it is necessary to simultaneously change it at more than 50% of these nodes. Such a simultaneous hack, of course, is theoretically possible, but unrealistic in practice.
Blockchain Trilemma Explained
The most obvious and fundamental solution to the problem of network congestion described above is to decrease the number of participants who confirm and add data to the network. This will enable increased scale and speed. But this will weaken decentralization when control is transferred to a smaller number of participants. This will also lead to weakened security, as fewer participants increase the attack probability.
Thus, a trilemma arises: given the inherent connection between decentralization and security properties, the fundamental design of the blockchain makes scaling challenging. By magnifying one, you weaken the other. How can scalability be achieved without compromising decentralization, security, or both?
Blockchain Trilemma Solution
There is no single golden solution to the crypto trilemma. But, given the importance of addressing this issue, several different approaches have been proposed in the community, yielding interesting results. Let's review some of the most popular developments to give you an idea of what's happening in this area.
Changes in the consensus algorithm
Today, there are various blockchain consensus algorithms, all of which partially solve the blockchain trilemma. They combine scalability, decentralization, and security to varying degrees. Apart from the well-known Proof-of-Work (PoW), there are also other consensus mechanisms such as Proof-of-Stake (PoS), Delegated Proof-of-Stake (DPoS), Proof-of-Burn (PoB), Proof-of-Capacity (PoC), Proof-of-Importance (PoI), Proof-of-Authority (PoA), Directed Acyclic Graph (DAG), Leased Proof-of-Stake (LPoS), Proof-of-Time (PoT), Proof-of-Elapsed Time (PoET), Proof-of-Space-Time (PoST), Simple Byzantine Fault Tolerance (SBFT), Delegated Byzantine Fault Tolerance (DBFT), and others. Blockchain creators choose a specific algorithm based on their network goals and tasks.
Level-1 Solutions
These solutions are directly related to modifying the blockchain itself, specifically its architecture. Developers offer various approaches and solutions to the blockchain trilemma.
For instance, they propose the utilization of multichains, the implementation of novel cryptography methods, sharding, and other techniques.
Sharding is probably the most popular approach. When using sharding, the main blockchain is divided into segments, each controlling its portion of the registry. Each segment is called a shard. In a network organization like this, each shard processes its own transaction pool, which increases network throughput. The main blockchain coordinates all shard activities.
Level-2 Solutions
Sharding and various consensus mechanisms are considered first-level decisions. They aim to fundamentally alter the network design. However, other developers seeking to solve this trilemma are working on solutions that build upon the existing network structure. In other words, they believe that the answer lies at the second level. Examples include sidechains and status channels.
Sidechain is a separate blockchain connected to the main network. It is arranged to transfer assets between them. Sidechains must work according to different rules, enabling increased speed and scalability. Similarly, state channels are another method of diverting transactions away from the main network and alleviating strain on the primary layer. The status channel utilizes a smart contract instead of a separate chain. This enables users to communicate with each other without publishing transactions to the blockchain. Only the start and end of the channel are recorded on the blockchain.
Conclusion
To fully realize its potential to change the world, blockchain technology faces the scalability trilemma.
If blockchain networks can only handle a small number of transactions per second to maintain decentralization and security, it will be challenging to achieve widespread adoption.
However, developers' methods to solve this problem suggest blockchain technology will continue to be used. In the future, these networks will be able to process more data.

